Bayard & Holmes
~ Jay Holmes
January 10, 2020 marks the passing of Sultan Qaboos bin Said al Said, the man who led Oman, the “other” Arabic country, for the past fifty years. We say the “other” Arabic country because by the standards of the region, Oman is a peaceful and happy place to live, which is something we can seldom say about that oil-rich corner of the world we call the Middle East. To understand a little about why Oman is not living up to the standards of mayhem and human suffering that most observers take for granted in that part of the world, it’s worth taking a glance at Oman’s history. We’ll do that with a timeline.
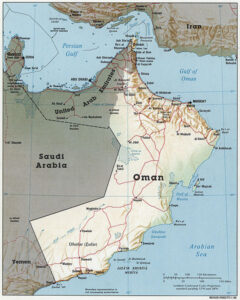
Image by CIA, public domain
OMAN HISTORICAL TIMELINE
6000 BC
Fire pit evidence indicates that people have arrived in Oman and stayed long enough to make a fire and eat a meal.
5000 BC
Non-nomads build fishing villages on the coast of Oman.
4500 BC
Pottery is produced in Oman.
2500 BC
Omani miners smelt copper, and Omani merchants set up trade with Mesopotamian trade ships. Copper is worth stealing, so concurrent with copper production and trade, large fortress construction starts in Oman to protect both mining and coastal areas.
2500 BC – 1300 BC
Oman continues to export copper and increases its boat making and seafaring skills as its neighbors evolve imperial domains such as Samaria and Ur. The increased sea trade to and from the Arabian Gulf benefits Oman.
1300 BC
Oman enters its iron age. Trade and wealth increase at a slow, but consistent rate.
1000 BC
Oman builds extensive irrigation ditches and, in doing so, becomes more “urban” as villages are able to support higher populations and develop more specialized skills. The irrigation technology may have been obtained from Persian immigrants. Oman begins to produce incense in commercial quantities for export.
300 BC
Wealth continues to accumulate in Oman. A classical period begins and sees an increase in commerce and art.
150 BC
Triliths are produced with inscriptions that remain undeciphered. The three stone structures are built in the interior of Oman in the frankincense-producing areas.
700 AD

Sultan Qaboos Mosque, Moscat, Oman
Image from CanstockPhotos
Bedouin Arabs enter Oman in greater number and bring Islam. Omani scholar Abu al-Sha’tha Jabir ibn Zayd al-Zahrani al-Azdi develops a moderate form of Islam known as “Ibadiyah,” which remains popular in Oman today. The Ibadi Muslims decide that while the Imam enjoys a high degree of control over the people, the people may vote to elect the Imam of their choice. The followers are entitled to impeach an Imam any time they decide to by simply voting to impeach him.
This is a notion that remains repulsive to modern-day Wahabis in Saudi Arabia, Shia junta members in Iran, Taliban thugs in Afghanistan, Al-Qaeda and ISIS leaders, and despots of any flavor throughout the world.
This great scholar died in 711 AD, but his birth date is unknown. Thank you Jabir ibn Zayd al-Azid. Your influence is still felt today in Oman and in the Gulf. R.I.P.
1500 AD
Portugal becomes interested in the Gulf region and seeks to control trade throughout the area. Portugal uses amphibious tactics to attack, sack, and occasionally capture various ports in southern Arabia and in eastern Africa.
1508 AD
Afonso d’Albuquerque conquers the critical port city of Muscat on the coast of Oman.
1518 AD
In a well-executed campaign, Afonso captures Hormuz and throttles non-Portuguese trade through the Gulf of Arabia.
1650 AD
The Iberian Empire is busy throughout the world and is unable to reinforce Portuguese forces in Oman. The Portuguese are evicted, but they do not all leave. Many Omanis had established cordial relations with the Portuguese, and some of their descendants remain today as a distinct ethnic group in Oman. They are allowed to practice Christianity unmolested by the Islamic majority.
1700 AD
The Omani Sultanate is powerful enough to extend its reach and build a large fort on the island of Zanzibar off the coast of Tanzania in East Africa. Oman becomes a major slave trading area.
Oman builds two distinct cultures. The inland Omanis are more conservative and isolationist, but continue to practice moderate Islam. The coastal Omanis develop a more international view and a more international culture. The differences in culture cause strife at times.
Oman gains a three hundred square mile colony in the Gwadar Peninsula in what is now modern day Pakistan. Gwadar prospers due to pearl diving and a particularly lucrative slave trade that sends Persian and Central Asian women to Arabia for high prices.
1815 AD
When Britain tires of Wahabi Arab pirates taking British East India Company ships, Oman and Egypt side with the British and conduct a successful campaign against the Wahabi pirates.
1834 AD
Oman has strong, friendly ties with the United States of America as well as Great Britain. President Andrew Jackson has special silver dollars minted for the Sultan of Oman.
1840 AD
The Sultan of Oman moves his seat of government to Old Fort in Zanzibar.
During the remainder of the 19th century, questions of dynastic succession and competition between Imams in the interior of Oman keep Oman busy and detract from trade profits.
1907 AD
Great Britain heavily influences Omani politics and forces Oman to end the practice of slavery. In the early decades of the 1900s, the more conservative interior Omanis gain a degree of autonomy from the less conservative government of Oman.
1954 AD
A new Imam comes to power in the interior of Oman and attempts to reject the central control of the Omani government. With the help of the British, Oman’s central government defeats the Imam in 1957.
In particular, the British Special Air Service made tremendous contributions in dealing with the rebels in the dry mountains of the interior. The Saudi government had clandestinely supported the rebels and continued to do so after their defeat. The Saudis and other Arab states did not abandon the unprofitable effort until the 1980s. Oman will likely not forget the Saudi support for the Islamic rebels for a long time.
1964 AD
Soviet-backed rebels operating out of South Yemen attempt to generate a communist rebellion in Oman. The communist rebels prove to be more adept at controlling their Soviet controllers than the controllers are at controlling their insurgents. The rebellion eventually dies in 1975.
1965 AD
Oil is discovered in Oman.
1967 AD
Oil production begins in Oman.

Sultan Qaboos of Oman, May 21, 2013
Image US State Dept., public domain
1970 AD
Qaboos bin Said Al Said conducts a bloodless coup against his father, Sultan Said bin Taimur.
Qaboos was educated in India and England. He was a graduate of Sandhurst Military Academy and, unlike Moammar Gadhafi, the Academy staff remembers Qaboos attending and graduating. Qaboos served in the British Army in a Scottish regiment and was posted to Germany for a year. After leaving the British Army, he continued his studies in England and traveled widely.
Qaboos introduces liberal reforms and forms a council to be elected by business leaders and prominent citizens.
1979 AD
Oman is the only government of an Islamic-majority nation that recognizes Anwar Sadat’s peace treaty with Israel.
1984 AD
Oman joins the new Gulf Cooperation Council, along with the United Arab Emirates, Kuwait, Bahrain, Qatar, and Saudi Arabia. The forming of the council is symbolic of the Gulf States deciding to bury their differences in favor of a united defense against Iranian military threats.
1986 AD
Oman’s first university opens. Emphasis is placed on science and on training teachers and nurses.
1990 AD
Sultan Qaboos announces a modern constitution which includes basic human rights for its citizens.
1996 AD
A census of Oman indicates a population of about two million.
2000 AD
Approximately 100,000 Omanis are allowed to participate in the selection of an 83-member council that will act as a “lower house” in a bicameral central government. Two women are elected. The Sultan selects the 48-member “upper house” and includes five women in the council.
2005 AD
An Omani court convicts thirty-one Islamic radicals of attempting a coup.
2012 AD
The history of Oman has resulted in a country that, while surrounded by anti-democratic governments and xenophobic cultures, has remained open to outsiders. Oman keeps cordial communications with Iran, and when Western governments wish to speak to the Iranian religious junta, they often do so through Omani diplomats. Western travelers have rarely encountered trouble in Oman. Islamic radicals are a small, shrinking minority and are not well-tolerated by the majority of the people or by the government. Oman makes no effort to stop anyone from practicing any religion. The minority Hindus and Catholics mix socially and professionally with their Islamic neighbors with no sign of segregation or hostilities. Neither the government nor the people of Oman have any interest in Islamic radicalism or any other fad in despotism.
At this point, Oman is a country trying to survive its radical neighbors while preparing itself for the loss of oil revenues that will occur in this decade. It is diversifying its economy. A major natural gas processing plant and port facility is being constructed with the help of British and American engineers. Since Sultan Qaboos came to power, education has grown rapidly, and literacy is at eighty-two percent and rising. Compared to Detroit and many other cities in the United States, these folks are Ivy League elitists.
Under Sultan Qaboos, Oman still had problems with unemployment, but protests were small, involving less than two hundred protesters. On one occasion, at least one protester was killed by a rubber bullet that struck him in the head. Qaboos responded by agreeing to more reforms and more jobs. The protesters in Oman under Qaboos were too few in number, and they did not appear to have any popular support.
March 2013 AD
Sultan Qaboos announced pardons for thirty-two anti-government protestor organizers and activists who had been convicted in 2012.
May 19, 2014 AD
In a landmark case, Oman’s former commerce minister Muhammad bin Nasir Al-Khusaibi was convicted of corruption. He was sentenced to three years in prison and a one million dollar fine for receiving bribes for construction work on the new Muscat International Airport. Former Omani Undersecretary for Transport and Communication Mohammed Al-Amri was also convicted of corruption concerning the same airport construction fiasco. He was sentenced to prison for three years and fined $3.1 million. For government officials anywhere in the Arabian peninsula to be held accountable for corruption is highly unusual and a hopeful sign for Oman’s future.
August 10, 2016 AD
Three journalists of the private Omani national newspaper Azaman were arrested for publishing an article alleging inappropriate government pressure on judges. The government claimed that the allegations were false and slanderous. Critics saw it as evidence that Oman lacks anything approaching free speech for journalism. Government supporters claimed that the newspaper was engaged in anti-government propaganda on behalf of foreigners. The Western media ignored the case.
June 2017 AD
In the midst of Qatar’s continuing political conflict with Saudi Arabia, Kuwait, and the United Arab Emirates, Oman allowed Qatar to use Omani ports to transfer cargo, thus bypassing sea, land, and air transport restrictions imposed on Qatar by its neighboring Gulf States.
October 5, 2017
The Omani Supreme Court ruled against the Azaman newspaper and ordered it permanently closed.
October 25, 2017 AD
New members of the consultative Majlis Ash’shura were elected. Several women campaigned for office, but only one woman was selected.
2019 AD
The government of Oman spoke openly about financial problems caused by the continued low oil prices. Oman’s credit ratings declined.
January 10, 2020 AD
Sultan Qaboos bin Said Al Said passed away. Sultan Qaboos’s cousin Haitham bin Tariq Al Said was sworn in as the new Sultan of Oman.
January 11, 2020 AD
In his first address to Oman, Sultan Haitham bin Tariq announced that he intended to continue with Oman’s long tradition of peaceful and moderate foreign policy, and that he intends to develop new economic programs to help Oman out of its current economic difficulties. Tariq is Oxford educated and has a reputation for being moderate, honest, and exceptionally intelligent. He has two decades of experience in quiet diplomacy on behalf of Sultan Qaboos and is well respected by foreign policy experts around the world.
Sultan Haitham bin Tariq faces great challenges.
On Oman’s southwestern border, Iranian-backed terrorists are fighting a brutally violent war with a weak Saudi-backed Yemeni government. On their northwestern border, Oman’s neighbors in the United Arab Emirates are facing new internal opposition. Twenty miles from Oman’s northern-most islands, the radical Iranian government continues to support terror groups across the region. Tariq will have to continue to skillfully handle Oman’s foreign policy while improving Oman’s economy. For the moment, he has wide support from Omanis.
Tariq also has one very important ace up his sleeve.
Oman has a new and vast refinery and port facility at Duqm on the Indian Ocean. The port facilities are continuing to grow, and China and several Western logistics companies have signed agreements with Oman for access to the new port. The Duqm port is quite valuable, as it will allow China and Western countries to access Gulf oil and natural gas supplies without having to venture near Iran’s coast or pass through the Straits of Hormuz. At the same time, dry goods from the West can be offloaded in Duqm and continue overland to the Gulf States. Duqm is a rare instance where China, Japan, South Korea, Taiwan, Australia, New Zealand, the United States, and Europe all find themselves on the same side of an important development. While the United States is currently a net oil exporter, any development that reduces Iran’s ability to threaten the world’s oil trade is good news.
The sooner the massive new Duqm port can increase its cargo traffic, the sooner Tariq will be able to stabilize Oman’s economy. Holmes’s best guess is that Sultan Tariq will succeed in improving Oman’s economy and will keep Oman independent and moderate.
* * * * * * * * * * * * *
Now on pre-sale!
SPYCRAFT: The Good, the Bad, & the Booty, Key Figures in Espionage

Hollywood has yet to produce either heroes or villains that can match the heights and depths of humanity. Who is more courageous than a one-legged woman, “the most dangerous spy in all of France,” operating in Nazi-occupied territory? Who is more extraordinary than a young man left for dead, not worth a Viet Cong bullet, who survives to hunt down terrorists for six more decades? Who is more heroic than a homeless child living in a cardboard box who grows up to be an iconic showgirl, an espionage legend, and a tireless humanitarian? And what villain is more malevolent than the traitor that lurks in our midst, walking our halls and eating at our tables, while helping our enemies murder our own and butcher thousands of innocents?
Join us as we explore the lives of these espionage elites and others who prove that “we’re only human” is not an excuse to fail, but a reason to succeed.
AMAZON KINDLE
OTHER DIGITAL OUTLETS









 Many Israeli politicians and military people were against the payments.
Many Israeli politicians and military people were against the payments.